- Strong - difficult to guess or brute force
- Unique - loss of a password for one system should not compromise others
- Usable - easy to remember, easy to input on a variety of devices
One recommendation covers best practice password management for 99% of scenarios - use a password manager. Meeting the first two requirements of good passwords may be easy - randomly peck at the keyboard for long enough and you’ll eventually have a strong unique password - but entering the result when logging in with your phone is likely to be a challenge at best. A password manager requires you to remember and use only a single strong password, and the application will manage strong unique passwords for the rest of the services you use. There are personal and enterprise options available with various combinations of features and pricing, all that remains is to find-one-that-suits-you.
There are other possible scenarios to consider, ordered for increasing levels of paranoia.
Some Paranoia
Alternative Password Systems
There are circumstances in which a password management application may not be a silver bullet solution. For example, a restricted environment may mean you can't install or access a password manager. In such circumstances techniques such as algorithmic passwords or passphrases (or a combination) may reduce your risk - though truly random passwords and a password manager are far more secure - use them whenever possible.
Algorithmic passwords replace the requirement to memorise unique strings of random characters with the requirement to create and memorize a single process for recreating your password whenever you need it. A seed password may be a part of the algorithm and include characters to meet the requirements some systems have, e.g. upper-and lower-case letters, a number and a symbol. The rest of the password is generated by various rules based on the characters in the service name, e.g. replacing them with related numbers or using adjacent letters on the keyboard. This does generate technically unique passwords for each service, but the loss of multiple passwords to a single attacker could make the algorithm possible to deduce.
| Algorithm | Google Example | LinkedIn Example |
|---|---|---|
| Last letter of service name | e | n |
| 50 minus the second letter in name's position in alphabet | 35 | 41 |
| Seed password "o-5W" | o-5W | o-5W |
| Shift+keyboard character above second-last letter of service name | O | * |
| Concatenate | e35o-5WO | n41o-5W* |
Algorithmic password example - note real use should generate a much longer password
Passphrases are another option, based on the fact that a short phrase of common words is both easier to remember and harder to crack by brute-force methods than common passwords based on a single word with some simple substitutions and added characters. A testament to their memorability is that I don’t need to refer to the source to report that XKCD uses the example of "correct horse battery staple" as a passphrase "you've already memorized". The usability of these is reduced by many systems being designed with a maximum password length far shorter than a passphrase would require plus requirements for special characters to be included.
It’s also possible that an attacker known to you might be able to guess the words you would use in a passphrase. To avoid this risk, a common solution is to use a Diceware passphrase, which allows the random selection of words by rolling a dice 5 times to generate a 5 digit number and selecting the corresponding word from the list. Diceware recommends 6 words for a standard passphrase, and 7 for high-risk accounts.
Two-Factor Authentication
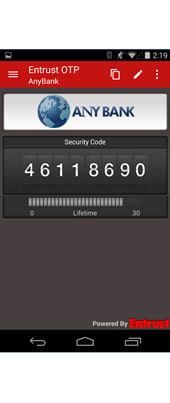

Two-factor authentication (2FA) increases security by requiring both something you know (i.e. your password) and something you possess (the 2nd factor) to authenticate. The second factor is commonly a short-term code presented via a dedicated security token (e.g. RFID tag, USB stick or RSA SecurID), or sent to a mobile phone by SMS or an app. The short validity makes it unlikely a brute-force attacker could guess the code before it expires and a new code is required, so the phone/dongle must be physically in your possession to use it.
This prevents the loss of a password from being sufficient to compromise an account, at least completely. The extra overhead of the second code is often only required for actions that would lock the initial user out of an account permanently like changing the password recovery email address. This depends on the way it's implemented by each system but secure passwords are still a requirement to prevent loss of privacy.
Despite any disadvantages it's worth enabling on any system that supports it. It's important to ensure that the second factor will be accessible when you need it though. If you travel without a roaming plan, don't get stuck needing a 2FA code via SMS to manage your bank account!
Serious Paranoia
Account Recovery Systems
As passwords become stronger, other avenues to access a target account become increasingly attractive. Account recovery systems can be worth considering as a potential vulnerability of your accounts.
If a service has a “security question” process, like requiring you to configure some additional proof-of-identity questions on account creation such as your first school, mother's maiden name and first pet, it can be a serious vulnerability as these can often be found with a cursory browse of public social media profiles.
Many services provide support for lost accounts, and may reset passwords on request when certain information is provided. This could be a problem - sometimes information that will allow one service's password to be reset, is information a different service makes public. Having multiple services reference each other can lead an attacker to breach them one by one.
2FA resolves most of these issues, ensuring you physically have something as well as knowing the correct answer. For services that don't support these and still ask security questions, there's no reason these can't be treated like ordinary passwords, they're just extra things you have to be sure to remember - so you can tell them your first pet was "f^cj?u+Z9.[f". Best to use a password manager again.
Digital Legacies
We're pretty well bombarded with messages to keep passwords secret, secure, locked away and hidden. It's likely that eventually we (or at least our families) may wish we'd planned to share them when necessary.
Death or incapacitation can present a significant burden to one's survivors on top of the obvious other issues they'd be dealing with. Along with a will and any other standard arrangements, consider planning to pass on your passwords.
Some services have their own ways to manage this, such as Facebook legacies and Google inactive account manager. Many won’t though, so it may be worth investigating whether you need a dedicated digital legacy product. Some password managers may include this feature.
Tinfoil Hat Territory
Dummy Accounts
As good as your technical password management strategies are, there's the (probably far-fetched) possibility of being a victim of rubber-hose cryptanalysis - or, an attacker physically coercing you to log into an account for them to take over.
Until login mechanisms that test you’re in a relaxed physiological state before granting access become mainstream, a possible solution is to set up dummy accounts. This would enable you to hand over real credentials to a less valuable account in the hopes that an attacker believes it to be the only account you have, leaving more valuable accounts alone. The only question is whether it’s worth the difficulty and expense in setting up a second account that looks legitimate.
Accounts? What accounts?
For the most serious paranoiac, the only answer is probably to go off-the-grid and live in the woods.
[As written by one of our Consultants]